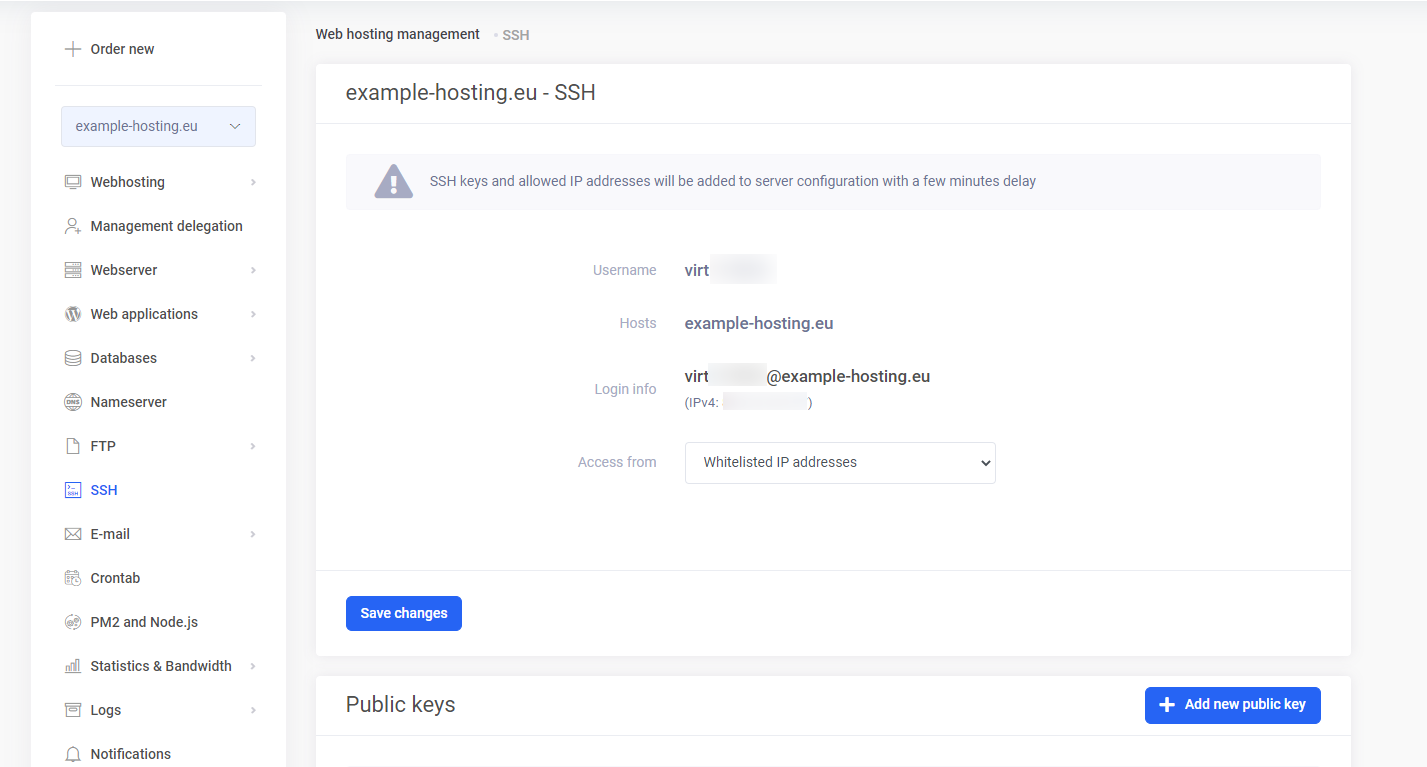
You can get an overview of SSH via server management.
The SSH access log can be accessed via the “Logs” section.
Zone is using asymmetric encryption (public key cryptosystem) instead of the usual password to authorize SSH users. You can find the “fingerprint” of the public key for each of the available algorithms in the SSH control panel.
The system performs authorization with a key pair, the public key is copied to the virtual server, and the private key remains with the user.
These algorithms are supported using the public key: RSA, ECDSA, ED25519.
Public keys must use the OpenSSH-compatible format (e.g. ssh-ed25519 AAAA…).
By default, SSH access is allowed from whitelsited IP-adresses but you can allow access for everyone. The list of allowed IP addresses can also contain blocks of IP addresses described in the CIDR format, which allows using an entire network (or several networks) instead of one IP-address.